RONIN
CLOUD SECURITY
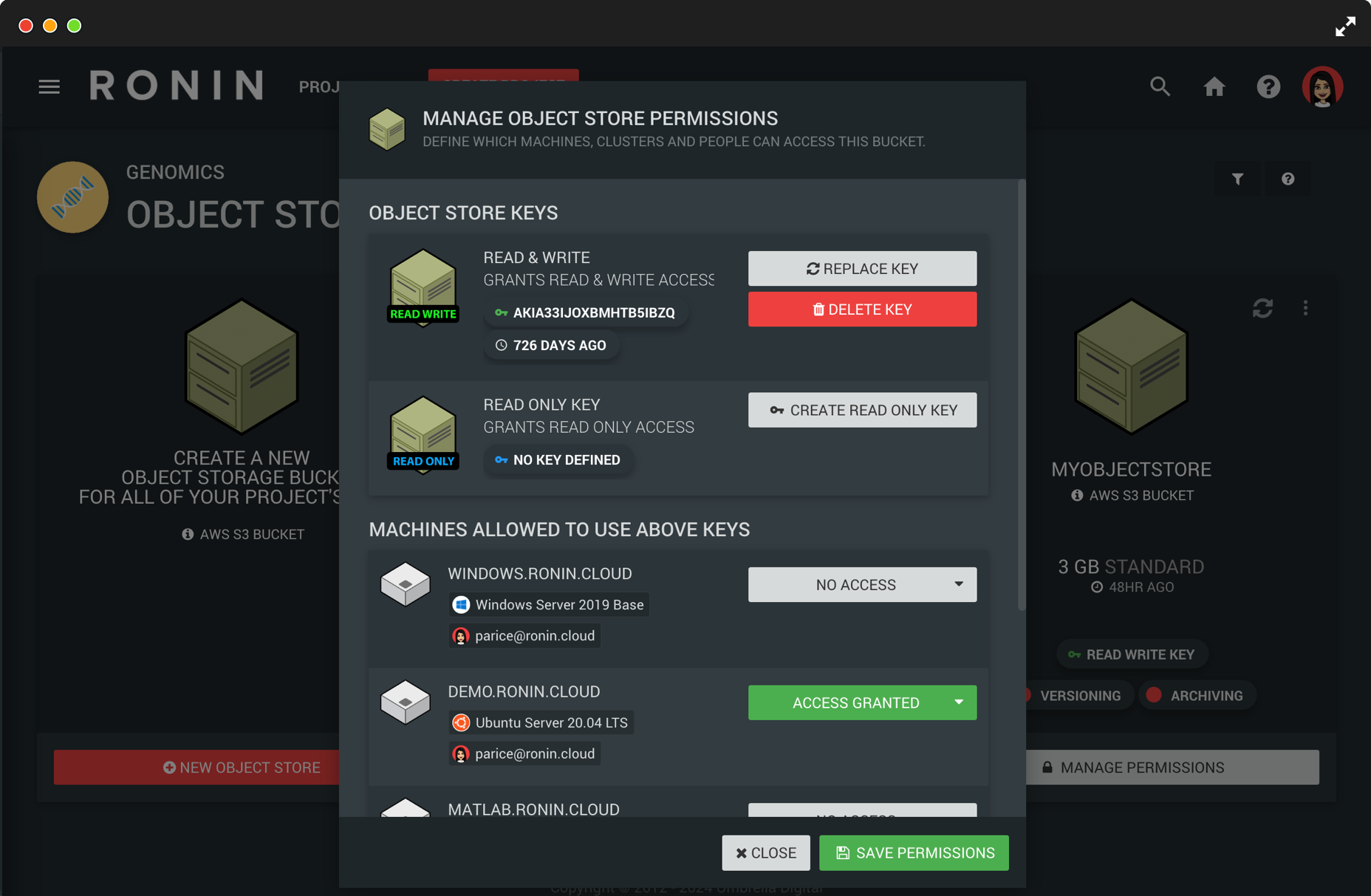
RONIN has been designed with security front of mind, whilst still maintaining a user-friendly experience. RONIN provides a configurable baseline of policies, controls and guardrails required to best position your organization to meet both regulatory and institutional IT security requirements.
RONIN automates complex security capabilities and granular protection of data thorugh network isolation rules and heirachical permission groups so that every action a user takes can be audited and will automatically comply with your defined security posture.
-
What is cloud security?
Cloud security encompasses a set of policies, technologies, controls, and procedures designed to protect data, applications, and infrastructure associated with cloud computing.
-
Is RONIN compatible with other cloud security solutions?
Yes, since RONIN follows AWS best practices within your account, RONIN is fully compatible with additional security controls provided by other AWS services such as AWS Trusted Advisor or AWS GuardDuty, or other third party software.
-
What are the benefits of cloud security?
Cloud security provides numerous benefits that enhance the overall safety, reliability, and efficiency of cloud computing environments including:
- - Data Protection
- - Compliance and Regulatory Adherence
- - Risk Mitigation
- - Improved Incident Management and Disaster Recovery
- - Better Operational Efficiency
-
How can RONIN help?
RONIN provides a configurable baseline of policies, controls and guardrails to best position your organisation to address any security and compliance requirements. RONIN automates all permissions, security groups, IAM policies, bucket policies, networking rules, data encryption, and abstracts these from users to ensure that every action a user takes complies with your pre-defined security posture. Every action in RONIN is also logged and can easily be audited using our own administration tools or exported for ingestion into other third party software.

